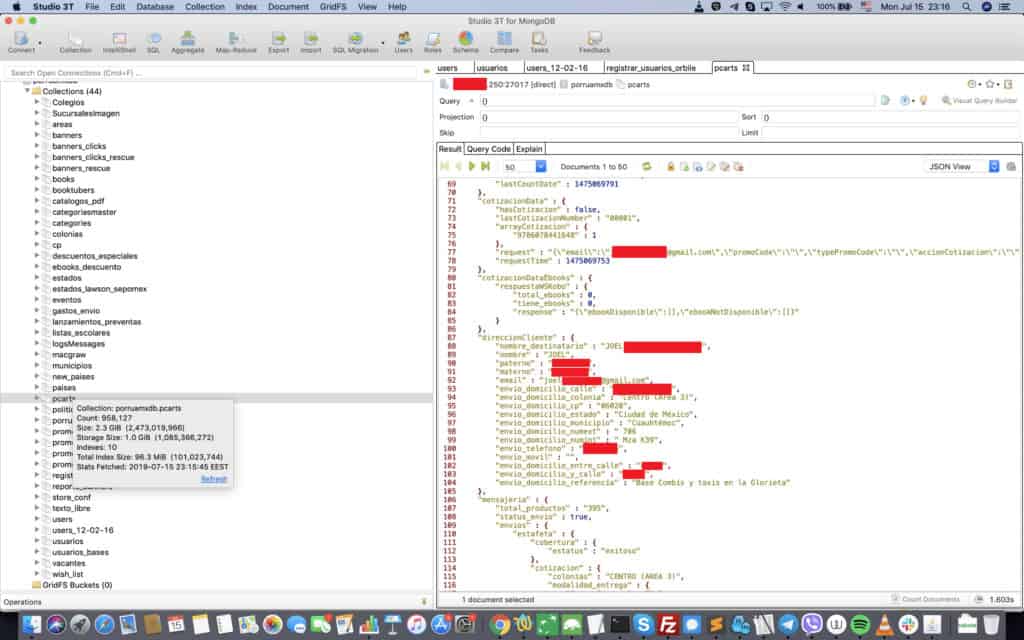
Hackers breached Librería Porrúa, a long-established bookseller based in Mexico, which exposed millions of customer records to the public. Security researcher Bob Diachenko collaborated with Comparitech to uncover the publicly accessible MongoDB instance before the breach occurred, but the company failed to take it down before hackers apparently accessed it.
The database included shopping records, users’ contact information, and other data.
Hackers breached exposed database before it was shut down
The database was accessible at two separate IP addresses, making it even easier to find. Anyone could access the database without a password or other authentication. Neither Comparitech nor Diachenko have received a response from Librería Porrúa at time of writing.
Here’s what happened, step by step:
- July 14, 2019: The database was first indexed by search engine Shodan.io.
- July 15, 2019: Diachenko discovered the exposed database and immediately notified the company.
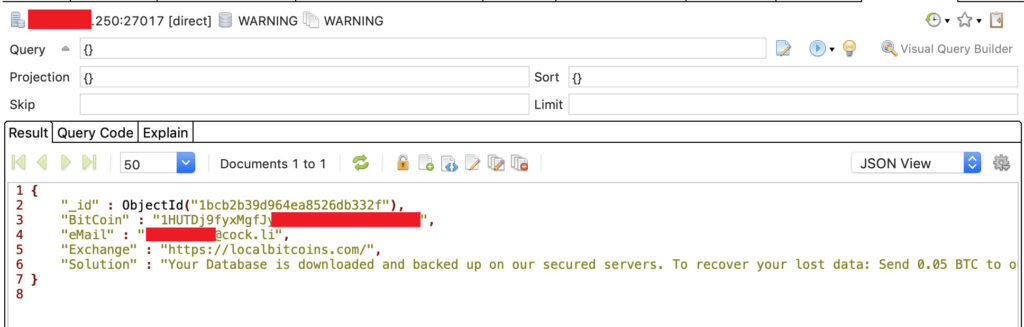
- July 18, 2019: The contents of the database had been wiped out and was replaced by a warning message. The message indicated hackers had stolen the data and demanded a ransom be paid in bitcoin.
- July 19, 2019: Public access to both the (now empty) original and cloned databases were disabled.
- July 29th 2019: Contact form on Librería Porrúa website not functioning correctly so we submitted a request for comment on this report via Twitter.
- July 30th 2019: Contact form submitted on Librería Porrúa website requesting a comment.
The ransom was 0.05 BTC, or roughly $500 at time of writing.
It’s not clear whether Librería Porrúa paid the ransom, but even if it did, that doesn’t mean the information in the database is secure. The hackers could still have a copy stored elsewhere.
What information was breached?
The exposed data included two sets of records: purchase records and users’ personal data. The former consists of almost 1.2 million records including:
- Invoices with purchase details
- Shopping cart ID
- Hashed payment card info
- Activation codes and tokens
- Full name
- Email address
- Shipping address
- Phone number
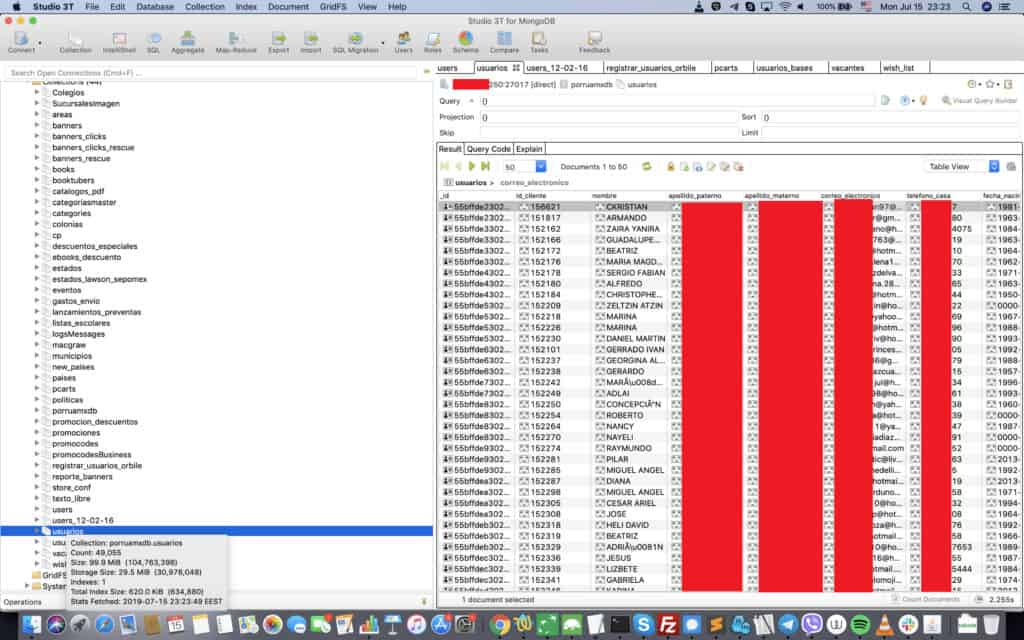
About 958,000 personal data records included:
- Client ID
- Full name
- Date of birth
- Email address
- Phone number
- User tokens
- Discount card activation codes
- Discount card activation dates
- Other info
Although we know how many records were leaked, we do not know how many users were impacted. For example, a purchase record and personal data record could belong to the same person.
The activation codes and dates appear to be for the company’s “Professor Porrúa” loyalty program, which gives a 15 percent discount to accredited active teachers at public and private schools.
About Librería Porrúa
Librería Porrúa started off as a brick-and-mortar bookseller and publisher in 1910, and today operates more than 60 commercial libraries throughout Mexico. The Mexico City-based company specializes in Spanish-language literature. Its digital storefront is a relatively recent addition.
Exposed databases threaten past and future users
Diachenko, who collaborates with Comparitech on security research, explains the dangers of exposing databases such as MongoDB or NoSQL without a password or other authentication:
“I have previously reported that the lack of authentication allows the installation of malware or ransomware on the MongoDB servers. The public configuration makes it possible for cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place, criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.”
The people whose information was exposed could be at risk of spam, targeted phishing, and fraud. If you’ve registered an account on Librería Porrúa’s website, be on the lookout for these attacks.
For example, affected users might receive emails claiming to be from Librería Porrúa with a link to a fake Librería Porrúa website. Users might be directed to enter login details on the identical fake website, giving hackers their passwords.
How and why we discovered this breach
Our security research team scans the web for vulnerabilities and data leaks. We aim to help organizations fix these issues and in turn make the internet safer.
Bob Diachenko, who uncovered the exposed database and subsequent breach, uses his extensive cybersecurity experience and knowledge to find supposedly secure data that may have been accidentally or intentionally exposed. When a leak is discovered, his first priority is finding out to whom the data belongs and alerting the relevant organization so they can secure it.
We then investigate the exposure further to determine the contents of the data and to whom it pertains. We disclose our findings in the interests of transparency and alerting impacted users so they can take any necessary action.
Previous reports
We recently reported on several other data leaks, including one involving the records of 7 million K-12 students, the personal information of 188 million people, and 300,000 records exposed by cryptocurrency exchange QuickBit. You can also read our articles on the biggest data breaches in history and the states that have the most data breaches.