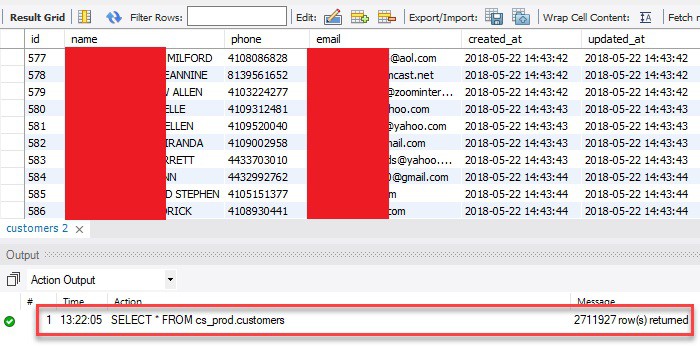
Friendemic, a customer management and digital marketing service primarily aimed at car dealerships, exposed more than 2.7 million consumer records on the web without a password or any other authentication required to access it, according to Comparitech researchers.
Researchers discovered the publicly accessible data on September 12, 2020. The consumer records included names, phone numbers, and email addresses, among other information.
Friendemic acknowledged the incident, advised that the database was an archive backup, and acted quickly to secure the data shortly after our notification of the exposure. It provided the following statement via email:
While no company ever wants something like this to happen, we are glad to have the vulnerability fixed. Thank you for notifying us and acting professionally. We have also notified our clients of the situation and have been doing a thorough review and enhancement of our data security.
Timeline of the exposure
We do not know how long the data was exposed for prior to Comparitech’s discovery. Here’s what we know happened:
- September 12, 2020: researchers discovered the database and began an investigation.
- September 14, 2020: Friendemic was identified as the owner. Researchers notified the company.
- September 15, 2020: Friendemic secured the data.
We do not know if any unauthorized parties accessed the data while it was exposed.
What data was exposed?
The data was stored in an Amazon S3 bucket. It appears to be an SQL dump or a backup copy of an SQL database, which is usually created for the purpose of migrating a server. SQL is a programming language commonly used to store and retrieve data.
The bucket included:
- 2.71 million consumer records containing personal information
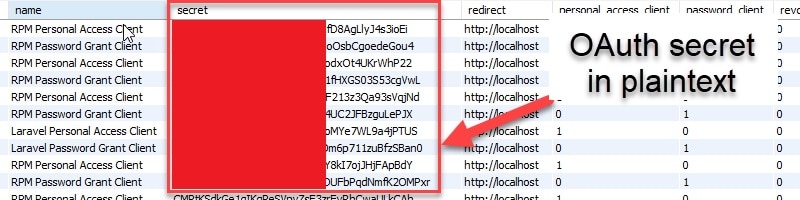
- 16 OAuth tokens stored in plaintext
- SQL dump of a schema used to run a web app
Each consumer record contained all or some of the following details:
- Full name
- Phone number
- Email address
It is not clear who the information belongs to. It initially appeared that the data pertained to car buyers, but Friendemic tells us that’s not the case.
Friendemic also told Comparitech the OAuth tokens were no longer in use when the data was exposed. But the fact that they were stored in plaintext in the first place raises questions about Friendemic’s cybersecurity practices.
Friendemic didn’t confirm what the tokens were for, but it did state:
“The tokens you saw were inactive tokens for other internal Friendemic systems. No Google OAuth tokens or tokens to any other external system were in the archive.”
The SQL dump containing a schema for a web app appears to be for Friendemic’s “Content Fuel” app. The app is used by car dealerships to collect content from staff that can be used for social media posts.
Dangers of exposed data
Consumers whose personally identifiable information (PII) was exposed should be on the alert for targeted phishing messages sent to their phones and email inboxes. Fraudsters may pose as Friendemic, a car dealership, or a related company and use personal information to tailor their messages. Do not click on links in unsolicited messages and always verify the sender before responding. Scammers might attempt to trick victims into giving up passwords, payment details, or other sensitive data.
Criminals could cross-reference the PII with other databases to learn more about potential victims and make their phishing messages more convincing.
About Friendemic
Friendemic’s suite of services are used for consumer relationship management, reputation building, and digital marketing. The company primarily serves car dealerships in the US.
Services include managing online reviews, social media advertising, sales analytics, and video sharing.
US-based Friendemic was founded in 2010. It merged with GoFanbase, another social media reputation management company, in 2017.
Why we reported this data incident
Comparitech researchers regularly scan the web for exposed databases containing personal information. When we find unsecured data, we begin an investigation to find out to whom it belongs, who might be affected, what data is exposed, and what the potential impact might be.
Once we determine who is responsible for the data, we immediately notify them so it can be secured as quickly as possible. We then publish a report like this one to raise awareness about data exposures and curb potential harm to people whose data was exposed.
Previous data incident reports
Comparitech has published several data incident reports like this one, including:
- Gym chain Town Sports exposes 600,000 records of members and staff
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
- Over 2.5 million CenturyLink customer records leaked