As a Mac user, you may be less interested in securing your computer because all of the attacks you read about seem to be directed at Windows computers. However, there is nothing about the macOS operating system that makes it immune to attack.
Many software utilities are available for both Mac and Windows, and they can carry malware. Internet connections produce security and privacy vulnerabilities that affect everybody, regardless of operating system.
Contents [hide]
Internet attacks are no longer just directed at companies. Any individual can have their lives ruined by malware, and these issues make computer security an important issue for everybody. Mac owners included.
Read more: Does Mac need antivirus?
This guide will explain the risks that currently threaten Mac users and how you can enhance your computer to guard against malware and online attacks. You will also find out about the intrusive methods that governments and marketers use and learn how to protect your privacy from everyday intrusion, not just keep your data safe from identity thieves.
Gatekeeper
Although the computer architecture of Macs has no special guards against malware, Apple has put a lot of thought into the features in its operating system that guard its customers against attack. Some of these protective features are optional and some Mac owners choose to disable them.
Since Mac OS X 10.8 Mountain Lion, the operating system has included a utility called Gatekeeper. This feature prevents programs from being installed unless they come from the Apple store.
See also: Best antivirus for Mac
Gatekeeper is a very effective block on unwanted malware. Apple is scrupulous about what apps it allows on its store. Each program is vetted right down to the code. That ensures no viruses or hidden malware can get onto your Mac. However, it also limits your options when sourcing software.
When prioritizing security for your computer, you have to guard against the unintended consequences of your own risk taking. Preventing the installation of software from anywhere will strengthen your protection against malware. Not only does Gatekeeper block software from untrusted sources, it keeps a database of performance warnings that highlight unsafe code. This database is called XProtect and is stored on your Mac. The XProtect file is updated periodically over the internet. So, your first task when making your Mac more secure is to make sure that you have turned Gatekeeper on.
Follow these quick steps to check on the status of Gatekeeper.
- Go to System Preferences and select Security & Privacy
- Click on the General tab and find Allow apps downloaded from.
- Activate the Mac App Store and identified developers option.
With this action you have already made your Mac more secure. There are many other cost-free easy actions that you can take in order to improve your Mac’s security.
MacOS security features
Apple increases the security of its operating system with every new version. You might wonder why the software developers didn’t get it right first time and find having to upgrade your Mac’s operating system an inconvenience. However, operating system updates are not just there to fix errors.
As time progresses, new threats to computers emerge and Apple keeps working to close down newly discovered vulnerabilities. Many upgrades shut down these “exploits”, so keeping your operating system up to date is an important action you can take in order to keep your Mac secure.
Apple made major changes to the Mac OS system in 2016 with the release of Sierra. The company even changed the name of the system from Mac OS X to macOS with version 10.12. The High Sierra 10.13 release is even more secure, so you should make sure to upgrade to this version of macOS in order to create a secure baseline for your system.
Malware threats to Macs
Just because there are more attacks on Windows computers does not mean that Macs are immune. In 2016, McAfee Labs reported (PDF) that virus attacks on Macs had risen by 744 percent that year. In total, MacAfee Labs found 460,000 different malware programs that targeted Macs floating around the world in 2016. The growth of malware for Mac continued apace. In August 2017, a report from Malwarebytes calculated that Mac malware had increased 230 percent since July 2016.
Although many people think of all unwanted, damaging, and invasive programs as “viruses” the definition of these attacking programs has become refined into several different categories and the umbrella term for these damaging programs is “malware.”
Malware types include viruses, worms, Trojans, remote access Trojans, rootkits, spyware, adware, ransomware and botware.
Viruses designed for Macs
Mac users always think that they are immune from viruses, but the focus of hackers on methods to attack Windows computers only occurred because there are a lot more computers running Windows than Macs. This was not always the case. In the early days of personal computers, Apple Macs had a much larger share of the market.
The very first “in the wild” computer virus was targeted at Macs. This was the Elk Cloner virus, which was created by a high school student in 1982.
Threats on Macs have escalated yearly ever since that first virus.
Microsoft Office macro viruses
The Microsoft Office productivity suite includes a collection of useful programs, which include the Word word processor, the Excel spreadsheet, and the Powerpoint presentation system. One major feature of all of these utilities is the ability to create macros. A macro is a series of commands that can be run to automate processes, meaning that you don’t have to type in the same sequence of commands over and over again.
Macros offer hackers a rudimentary programming language and they have managed to create malware with it. When you open a file that contains a macro virus, that malware gets triggered and performs its tasks on your Mac.
PC users have had to contend with macro viruses for a long time. Applications, such as Microsoft Office, Excel, and Powerpoint allow macro programs to be embedded in documents. Macros are able to call upon extra programming code, which means that they can extend their operations beyond the document that contains them. Macro viruses have been known to log keystrokes, take screenshots, and access webcams.
For a long time, Mac users were protected from the dangers of macros because the Office versions for Mac did not have macro capabilities. This ban was enforced from Office 2008 through to the release of the 2011 version.
The easiest way to avoid being attacked by a macro virus is to be cautious about downloading and opening Microsoft Office files that arrive from unknown sources. The opening program should warn you if the document contains macros. In this case, you should heed the warning and cancel the opening of the file.
Rootkits designed for Macs
This category of malware is able to get system privileges and use that status to take evasive measures to protect itself and its associated viruses.
OSX/Pirrit
This rootkit virus hid inside cracked versions of Microsoft Office and Adobe Photoshop. These cracked software versions can be downloaded and used for free because you don’t need to buy an activation key to open them.
OSX/Pirrit dates back to April 2016 and managed to continue in circulation without being spotted until early 2017.
Meltdown
Meltdown, together with Spectre, which is the next security weakness in this list was discovered in January 2018. This exploit was made possible by a procedural security weakness in the Intel chips used by Apple for its devices. The Meltdown exploit affects iOS devices as well as Macs.
Fortunately, Apple technicians spotted this system weakness before hackers did, so there is no actual Meltdown virus. However, after Apple publicized this problem, there could well be a hacker willing to put in the time to make the most of this weakness on the off-chance that not everyone installed the patch to fix it. So, it is better to deal with this problem before it turns into a disaster. Make sure you have macOS 10.13.2 or later to protect yourself from Meltdown.
Spectre
Spectre is the second Intel chip security weakness that was discovered alongside Meltdown. This also has never been exploited, so you need to get ahead of the hackers and close down this flaw before it becomes part of a hacker’s toolkit.
The details of Meltdown and Spectre are extremely technical. Meltdown involves a “rogue data cache load” and Spectre would be either a “bounds check bypass,” or “branch target injection.” The upshot of both flaws is that regular programs could access the operating system’s kernel and then bypass all security measures. These two weaknesses could even be accessed by JavaScript running in a web browser. So, any hacker wanting to get to your data wouldn’t need to download software onto your computer.
To block off the Spectre exploit, make sure you have the macOS 10.13.2 Supplemental Update. This update should have been installed automatically on your Mac by now.
Worms designed for Macs
Worms are very similar to viruses. One distinction between the two is that generally viruses are transported on physical media, such as a DVD or USB stick, while worms get onto a Mac over the internet. A worm is a virus that can replicate itself and spread over networks.
The characteristics of worms and Trojans are very similar and so the many instances of what would once have been described as worms, are not listed as Trojans.
Safari-get
This worm was spread by email. The effects of the virus depended on the version of the macOS operating system that the virus landed on. Despite the name, it does not infect the Safari browser. In some cases, the virus got into the Mail app and generated a vast number of draft emails, the other version opened up iTunes again and again. In both cases, the flood of processes caused the computer to overload and freeze.
The purpose of this worm was to scam Mac users into calling a fee-charging help desk for assistance. The tech support operatives, unsurprisingly, were able to fix the problem quickly.
This worm was first spotted by Malwarebytes in November 2016. Computers running macOS Sierra 10.12.2 and above are immune to this worm, so if you experience this behavior, upgrade your operating system to solve the problem.
Fruitfly
Although first spotted in January 2017, Fruitfly was suspected to have already been in operation for more than two years by that date.
When it gets onto a computer, it looks for addressing information about other devices connected to the same network and then connects to them, enabling it to download itself onto another target.
Fruitfly is able to access webcams connected to the computers that it infects and it periodically takes snaps. It also takes screenshots of the activity on a computer. The Gatekeeper system now blocks instances of Fruitfly from downloading onto a protected Mac.
X-agent
February 2017 was a big month for malware discovery. X-agent was one of the major viruses for Macs that was identified in that month. This malware has similar characteristics to Fruitfly because it takes screenshots periodically. Infection of Macs seems to be a sideline, because the main target of this malware was iPhone data. The malware captured passwords for websites and also copied iPhone backups stored on Macs.
The origin of this malware is thought to be the APT28 group — a hacker organization that is frequently employed by the government of Russia in its “hybrid warfare” tactics. The worm was targeted at Ukrainian military personnel.
OSX/Dok
Apple dealt with OSX/Dok very quickly after it was first discovered in April 2017. Hackers managed to acquire the Apple approval credentials of a software house, which enabled this worm to slip past Gatekeeper. On discovering this security breach, Apple revoked the compromised developer certificate and updated the XProtect database of all Macs to block OSX/Dok.
This worm is delivered through phishing emails. These are emails that pretend to be from well-known organization and encourage you to click on a link and log in to a faked web page.
The malware alters the network settings on an infected Mac. The infection phase nominates a proxy server for internet communications. With this setting all the internet traffic going in and out of that computer would pass through the designated proxy. This pass-through enabled the hacker to search, record, or alter any message he liked.
OSX/MaMi
Discovered in January 2018, OSX/MaMi has a very similar operating method to that of OSX/Dok. Whereas OSX/Dok changes your proxy settings, OSX/MaMi changes your DNS server. Your browser needs to translate web addresses, such as “comparitech.com” into an internet address before it can request a page from that website’s host. The DNS server delivers the correct internet address for a given domain, which is the root of a web address.
When your Mac is set up to use a DNS server that is controlled by a hacker, all of your internet traffic can be redirected through the hacker’s server.
This is very similar to the proxy server redirection method used by OSX/Dok. The beauty of both OSX/MaMi and OSX/Dok is that the software of the worm only needs to run for a few seconds. After that, it doesn’t matter if the worm is destroyed because the damage has already been done. Your security and privacy will be compromised at a location outside of your Mac and there is nothing that anti-malware can do to detect or prevent the ongoing operation of these scams.
There is one more action that this worm performs while it is briefly active on your computer: it installs a new security certificate. This certificate is part of the encryption system used for secure web connections using HTTPS. With your encryption system set to a cipher and key that the hacker can decrypt, you will be susceptible to fake web pages being delivered to you and all of your login and credit card details can be captured by the hacker as they pass through his server.
To see whether you have been caught by this trick, look in the network settings of your Mac and check the DNS settings. If either of the addresses 82.163.143.135 or 82.163.142.137 appears there, your security has been compromised.
Trojans designed for Macs
Whereas a virus attached itself to an existing program or media file, a Trojan can run as a standalone process. This type of malware is advertised as a useful program, but usually doesn’t perform any of the functions that it is supposed to. Sometimes a Trojan is bundled in with a genuine utility and gets onto the Mac through an installer program.
The best way to defend against this Trojan is to only download applications from the Apple store or direct from the sites of well-known software developers.
Backdoor.MAC.Eleanor
Anti-malware producer, Bitdefender discovered Backdoor.MAC.Eleanor in July 2016. This Trojan could be perceived as an “advanced persistent threat.” APTs allow hackers to retain access to computers, connect to them, and manually explore files and data as well as download automated spyware.
Backdoor.MAC.Eleanor is capable of accessing your webcam, taking screenshots, stealing files, and destroying data.
The initial invasion by this Trojan occurs through the download of a handy tool, called EasyDoc File Converter. The first disappointment any downloader experienced with this utility is that it just didn’t work. Naturally most people deleted the program. However, by then, it was too late: the Trojan had already installed access software, which opened up a connection from your computer to the Tor network.
One of the routine tasks that the Trojan performed was to send out spam emails from the victim’s account to all discovered contacts. This email was a replication mechanism of the Trojan and contained an infected attachment.
MacDownloader
MacDownloader was discovered in February 2017. The transport mechanism for this Trojan is disguised as an update for Adobe Flash. The installer for this fake update alerts users to the presence of adware, with an option to remove the problem. The installer than asks the user for the system password, which is the target piece of information for this malware.
Once it has access to your system, the malware searches out your keychain information, which is used for authentication on Apple cloud services. This also unlocks any credit card information stored on your Mac. With access to the internet, MacDownloader then uploads all of this sensitive information to its home server.
This Trojan was designed by Iranian hackers and was particularly targeted at the US defense industry.
Flash has become a notorious vehicle for malware. In fact, the video medium has become such a threat that it is now blocked from playing automatically on Macs. This is another example of a malware attack that can be easily blocked just by updating to the latest version of macOS and having Gatekeeper active.
Online attacks against Macs
The threats to your Mac’s security extend worldwide as soon as you connect it to the internet. There are security and privacy weaknesses during transfers over the internet that you should account for. Some threats require an element of programming code to be resident on your computer. The OSX/Dok and OSX/MaMi threats show that just a small adjustment in the network settings of your Mac can give a hacker access to all of your private activities.
Online threats to Macs fall into the following categories:
- Botnet enslavement
- DNS hijacking to capture and divert all internet traffic
- DDoS attacks against the servers you want to visit
- DDoS attacks against you
- Man-in-the-middle attacks where hackers steal your data in transit
- Advanced persistent threats, where hackers gain regular access to your Mac
Many of these intrusions go undetected. Reported online attack campaigns are probably the tip of the iceberg.
Man in the Middle attacks on Macs
In a man-in-the-middle attack, an interloper poses as the web server. Online encryption systems and authentication procedures are supposed to prevent these types of hacks. However, standard validation procedures on Macs have been found to have weaknesses.
Macbook users can be tricked when looking for a public wifi hotspot into connecting to a fake wifi service that is actually run by a hacker. In this instance, the authentication and encryption process is controlled by the interloper and so all of your communications can be read, altered, or diverted, which are the classic goals of a man-in-the-middle attack.
SSL Gotofail
Back in 2014 a bug in the validation procedures of internet encryption system exposed the communications of Mac users over wifi networks. This was dubbed the “SSL Gotofail error.” The HTTPS schema encrypts the contents of web page transmission, using an encryption cipher owned by the web server.
The browser gets this cipher key from a third party database and if the server can responds to a challenge message it proves its identity. This is because the process uses an asymmetrical key system where the decryption key and the encryption key are different. Only the true owner of the security certificate will be able to decrypt messages that have been encrypted with the public key displayed on the server’s security certificate.
The Apple program that implemented this authentication phase of a connection contained a bug. There was a GOTO statement in there that didn’t have a corresponding action. The result of this was that authentication failures were ignored.
The encryption procedures that define the authentication process are defined in the Secure Socket Layer, or SSL. This is why this security weakness was known as the SSL Gotofail error. SSL has since been replaced by Transport Layer Security and Apple spotted its program bug and fixed it, so you don’t have to worry about this weakness anymore.
Until the error was spotted, the failure of the authentication processes of SSL made users vulnerable to “man in the middle” attacks.
SSL is supposed to block this strategy because the interceptor would be unable to pass the encrypted challenge. As authentication failure didn’t block the continuance of the connection, hackers were able to send out a new encryption key to the browser of a victim. This is particularly easy to do over wifi networks.
Once the browser switched to the new encryption key, the hacker could decrypt all subsequent messages. SSL was used to protect web pages that require passwords and important ecommerce functions, such as online banking. So, this SSL Gotofail error allowed hackers to reap a lot of useful information. Apple fixed this error quickly for iOS 6 and iOS 7, but took longer to release the fix for Mac OS X. That patch finally came out in February 2014.
Botware designed for Macs
Not only are you at risk of being attacked over the internet but there is also a danger that your computer could be hijacked to take part in attacks on other.
This scenario is called a “botnet” and the computers that make up these groups of attackers are owned by members of the public who have no idea that their Macs have been turned into zombie computers.
Botnets are used to launch “distributed denial of service” attacks. DDoS attacks can bring down web servers, rendering them inaccessible by overwhelming them with too many requests all at once, blocking out legitimate requests. The hacker that controls the botnet rarely has direct contact with each zombie computer. Instead, malware on the computer checks message boards or parked web domains for instructions.
If you enjoy playing games online, you may have noticed that some games servers are almost impossible to connect to. There are two possible reasons for this. The first is that some games servers are constantly under DDoS attack. In order to combat these attacks, the server administrators sometimes ban large blocks of internet addresses from getting access. Your address may be included in one of those ranges, and so your enjoyment of the internet is impaired.
Worse still, the owners of botnet now offer a DDoS-for-hire service. Some gamers and victims of revenge attacks get directly attacked by these services.
A hired DDoS attack often only lasts for five minutes. However, if you are winning a poker match at that point, suddenly being blocked access to the internet can be a costly event.
Cryptocurrency miners have found a new use for botnets. They use the zombie computers to do all the mining. This pursuit uses a lot of processing time and also burns a lot of electricity. So, if your electric bill suddenly ramps up and your computer is active all the time, even when you are not doing anything on it, your Mac may be part of a cryptocurrency botnet.
Apart from cryptocurrency miners, botnet zombie activities require very little activity of each individual computer.
Flashback
Flashback created a botnet of 600,000 Macs. The botnet was assembled over a period starting in August 2011 but was not properly identified until April 2012. This was not the first botnet created for Macs. Early in 2011 a fake anti-virus scam created a large army of zombie computers, but that botnet got stamped out when its Russian creator, Russian cybercriminal, Pavel Vrublevsky was arrested.
The mechanism used to install botnet controlling software on Macs was called BackDoor.Flashback.39. This was a JavaScript exploit rather than an email trick. Apple created a security patch for Mac OSX in April of 2012, which closed off the JavaScript access to the Mac OS X operating system and greatly reduced the creation of botnets in that year.
Mac.Backdoor.iWorm
The Mac.BackDoor.iWorm botnet involved around 17,000 Macs — half of which were in the United States.
The benefit of botnets to hackers lies not just in the volume of traffic that they can create, but also in their anonymity. Hackers have developed a command a control system for botnets that embed instructions in the botnet program that tells it to look at third-party systems for instructions. In the case of this botnet, a program started running at system start up and then periodically checked a Minecraft server subreddit for instructions.
Anonymous posts to that Reddit message board would contain IP address. These were the addresses that the botnet would then attack. This method enables the hacker to remain anonymous because there is no direct contact between him and the infected computers. However, this botnet was successfully shut down when Reddit deleted the hacker’s membership account.
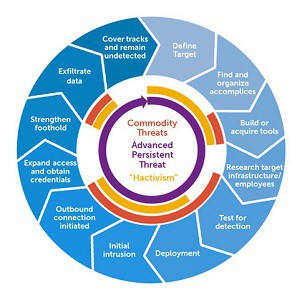
Advanced persistent threats against Macs
Advanced persistent threats often go on undetected for years. Even corporate networks with expert systems administrators become long-term victims of APTs without knowing it. APTs are implemented by “remote access Trojans.” This scenario is not just an opportunity for identity theft, but it can also turn your Mac into a zombie computer to attack others as part of a botnet.
OSX.PROTON
The original computer virus attached itself to a bona fide file and the OSX.PROTON virus went back to this delivery system in its attacks that occurred in May 2017. PROTON is a remote access Trojan, which gives the hacker complete control of your computer without you knowing about it. This enables the hacker to view your screen in real time, copy your files and download controlling programs onto your Mac.
The OSX.PROTON downloader was attached to the download system for a popular Mac video conversion utility, called HandBrake. The producers of HandBrake had nothing to do with the creation of the virus. They took down the mirror site that had been infected with the virus as soon as they discovered it.
If you installed HandBrake in May 2017 you can check whether your Mac has been infected.
Open Activity Monitor from Applications/Utilities and look for a process called activity_agent or Activity_agent. If you see that process, your Mac is under the control of a hacker.
To get rid of the virus, follow these steps.
Step 1
Open a terminal window and enter:
launchctl unload ~/Library/LaunchAgents/fr.handbrake.activity_agent.plist
rm -rf ~/Library/RenderFiles/activity_agent.app
Step 2
Look in the VideoFrameworks folder of your Library directory. If you see the file proton.zip there, delete the entire VideoFrameworks folder.
Step 3
Delete the infected HandBrake.dmg file and download it again.
Ransomware attacks against Macs
Ransomware encrypts all of the files on a victim’s Mac. The only way you can get access to these documents and media files is to pay the controlling hacker a ransom. Often, the hacker doesn’t deliver the solution, so paying doesn’t get you your files back.
Some scammers deliver a threat of an imminent threat, giving you the option of calling off the attack by paying the ransom in advance. However, in most cases, there is no planned attack in the pipeline.
The only way to protect yourself against ransomware attacks is to make regular backups of your files with a cloud server or on a memory stick.
KeRanger
The 2017 WannaCry attack on devices running Windows XP was a big new item all around the world. However, a major ransomware attack that targeted Macs occurred more than a year earlier without drawing the attention of the media. KeRanger encrypted all of the files on an infected Mac.
The owner would then have to pay a ransom in order to get the decryption key to regain access to those files. The price of recovering those files was set at 1 Bitcoin, which was worth $400 at the time.
KeRanger got onto computers through an infected copy of the Transmission BitTorrent client. This virus was contained within Transmission 2.90, which has since been taken out of circulation.
Surprisingly, the KeRanger program was signed with a valid Apple developer’s certificate, which meant it was able to get past Gatekeeper. Apple has since revoked that certificate and updated the XProtect library to detect and block KeRanger.
Patcher
The Patcher ransomware was a major attack on Macs that predated the famous Windows WannaCry attack by just a few months. This malware was also referred to as OSX/Filecoder. Macs got infected by this ransomware when users downloaded cracked versions of Adobe Premiere CC or Microsoft Office 2016. These files were made available over the BitTorrent system.
The first shock downloaders got was that the crack to access these premium software packages for free didn’t work. The second nasty surprise was the encryption of all of their files and a ransom demand. Victims could choose to pay 0.25 Bitcoin to get their files unlocked or 0.45 Bitcoin for the premium ten minute solution. Those sums equaled $280 and $500 respectively at the time. Paying the ransom doesn’t get your files decrypted.
There is no way to recover your files once they have been encrypted by Patcher. Even paying the ransom will not get them back. In the case of Patcher all you have to do to get rid of the ransomware is delete the Adobe Premier CC or Microsoft Office file that you downloaded. After deleting that program and all of your encrypted files, restore your original files from your backup.
SEE ALSO: Ransomware statistics
Antivirus and malware protection for Macs
Although the Gatekeeper system offers a great deal of protection, as you can see from the previous two sections, often Apple doesn’t know about new viruses. Many threats to your computer can originate from outside macOS, requiring deeper protection than just install controls.
Antimalware is becoming an important security tool for Macs as virus and malware attacks increase. You also need to take procedural steps to protect your Mac and guard your internet activities.
Comparitech has an in-depth feature on the best Mac antivirus programs. The recommended malware prevention systems listed in that article are summarized here below.
1. Kaspersky Internet Security for Mac
Kaspersky Labs constantly monitor for new malware and their efforts result in alerts that communicated to the public through online news services. The great benefit of installing Kaspersky Internet Security for Macs is that the company identifies and blocks malware a lot faster than most other antivirus companies. However, it is important to keep the system turned on and allowed to update automatically, otherwise you won’t get the full benefit of the rapid response feature of this protection.
Additional benefits of this software include a parental control system and website scanning for potential threats.
2. Bitdefender Antivirus for Mac
Bitdefender is another antivirus company that often spots new malware first. This malware protection suite is particularly strong against ransomware threats. Its features include extra protection for the Mac Time Machine backup system and also a double protection for special, nominated files on your computer.
3. Intego Mac Internet Security X9
Intego’s antimalware system was built from scratch for Macs, not adapted from a program originally written for Windows. It also includes backup protection. A downside of this useful protection is that Intego slows down system performance, particularly when you copy files. Additional protection included with the Intego package includes anti-phishing warnings and a location-based firewall.
4. ESET Basic Cybersecurity for Mac
ESET has a range of antimalware products to suit all budgets. The Basic Cybersecurity package is the entry-level version. You can give this malware protection system a spin with a 30-day free trial.
5. McAfee AntiVirus
McAfee is one of the top anti-virus systems in the world. Unfortunately, it puts all of its effort into making its product for Windows and its Mac version is a lot less comprehensive. However, McAfee AntiVirus for Macs still puts in a respectable performance.
6. Symantec Norton Security Standard
Like McAfee, Symantec is one of the leading antivirus companies in the world and its consumer brand, Norton offers strong protection. A major benefit of this antimalware system is that it has very little impact on the performance of the Macs on which it runs. However, that quality comes with a high price tag, which is why the Norton Security Standard didn’t get to the top of our list. If you have money to burn, you could also check out the Deluxe and Premium versions.
Tracking systems on Macs
Hackers, government agencies, commercial enterprises and stalkers have tracking utilities available to them that can help them trace all of your internet activities. These tracking systems record each of the websites that you visit and can really be counted as a form of spyware.
The majority of web advertising now relies on a system called retargeting. This method relies on tracking software. When you visit a website that participates in retargeting, it will copy a cookie onto your computer and store information on the pages that you visited and the actions that you performed there. When you move onto another website that participates in the same advertising scheme, that page will check on those tracker cookies and load in adverts that relate to the sites that you visited.
Trackers are not classed as spyware because they are important to the operations of commercial websites. So, just as spyware assists adware, trackers assist retargeted advertising.
You may find it difficult to tell the difference between respectable digital marketing technique and distrusted malware practices. There is a fine line between the two and many web surfers choose to install ad blockers and tracker blockers. This consumer action has caused great problems for online advertisers. However, despite this, Google Ads, the most widespread implementer of retargeting, has become the most lucrative division of its parent company.
Apple has noticed the preference for ad and tracker blockers in the Mac community and has taken steps to integrate these facilities in its operating system and in its Safari browser. Tracker and ad blocking are measures implemented in the browser. You can read more details of these in the next section of this guide.
Tracking is common to all computer operating systems. The ability of websites to download cookies onto your Mac derives from the fact that these little bits of storage and code have become essential to the operations of just about every website around. Most browsers allow users to block cookies completely, but then those surfers will find that the important sections of the websites that they visit will not load.
Just about every web page has a row of social media “Like” buttons. These seem cheerful and friendly and, in fact, their presence is built into just about every online web platform development template. However, the presence of these buttons is not so innocent. Every time those buttons load into a browser, they report back to their home server on your location, the web page that you are visiting, and your IP address.
Facebook, Instagram, and Twitter are constantly tracking all of your internet activities even if you are not a member of any of those clubs.
These tracking methods don’t even touch your Mac, so there is nothing that you can do on your computer to prevent those media buttons logging your actions. However, there are browser extensions that will prevent these buttons from loading, and so keep your web activities private from the social media giants. You can read about the problems of social media buttons and how to block then in the features article, How to stop Facebook tracking you across the web (step-by-step guide).
Privacy-conscious web users need to rely on browser extension in order to block tracking codes. The same is true for those who wish to combat the new tracking method of browser fingerprinting. Web technicians have discovered that the information that can be queried by a web server from a browser can give enough information to uniquely identify a visitor, no matter what evasive steps that surfer takes.
Web pages are delivered via a standard that is called the Hypertext Transfer Protocol. The codes in this message system include queries to find out the browser version, the default language, and the operating system and its version. There is actually a long list of attributes that a web server can glean about the software and hardware that a visitor has — these factors are called “user agents.” A combination of these attributes builds up a unique profile of each surfer — even those who change their internet address, block cookies and use tracker blockers. This profiling technique is called browser fingerprinting.
Browser fingerprinting can uniquely identify you and allow others to secretly track all of your internet activities.
Macs don’t include any browser fingerprinting blocking methods. The profiling tracking method is in the realm of the internet and browsers rather than in the operating systems of computers. So, if you want to block trackers and fingerprinting, you will need to install a browser extension.
You can read more about browser fingerprinting in the Comparitech feature article, How to protect yourself against invisible browser fingerprinting. Further on in this guide, you will find recommendations on extensions that can help you even the score and block browsers from sending out user agent information.
Even if all of the content of your internet communications is secured with encryption, the administrative data that manages the transport of each internet communication can give away some important information. For example the address of every website you visit has to be visible to all of the routers that your traffic passes through. That starts with the computers of your internet service provider.
In many countries, your ISP is obliged by law to record and store records of all of your internet activities. The ISP can also use the routing information on your connections to block or filter access to certain websites. There isn’t anything that macOS can do to help you get around this problem. This is an issue that needs to be dealt with through an online service. A system called a “virtual private network,” or VPN for short, can block off snooping and website access controls. You can read more about these services later on in this report.
First of all, take a look at your browser and check out which apps will give you the best security and privacy when surfing the web.
Browsers on Macs
When accessing the internet on a Mac, your first browser choice is likely to be Safari. However, all of the major browser brands run on Macs, so you shouldn’t limit your option to the Safari browser just because it comes ready-installed on your computer.
Safari has had some security failures in recent years. To be fair, the latest security scare directed at Safari was nothing to do with the browser itself. You have already read about the Meltdown and Spectre vulnerabilities that derive from loopholes in Intel chip operating software. This has been misreported in some places as a weakness in Safari.
In this section, we take a look at the Safari browser and weigh up which other browsers might be better in terms of security and privacy.
Safari
Thanks to the fast response of Apple on the discovery of the Meltdown and Spectre vulnerabilities, you should be safe from the latest potential security threats to your Mac as long as your Safari browser version is at least 10.11.6.
According to a 2017 study performed by Google Project Zero, Safari has more security weaknesses than Google Chrome, Internet Explorer, Microsoft Edge, and Mozilla Firefox put together. This is some claim, particularly as security concerns prompted Microsoft to replace Internet Explorer with the Edge browser and caused a flood of Microsoft browser users to switch to Chrome.
Google Project Zero discovered seventeen security vulnerabilities in the Safari browser. This figure compares to two vulnerabilities found in Google Chrome, four detected in Mozilla Firefox, four vulnerabilities in Internet Explorer, and six problems revealed in Microsoft Edge by the same study.
The problem with assessing browser security, however, is this topic is a moving target. Studies such as the Project Zero research quickly become out of date. For example, since September 2017 when this report was released, Mozilla has produced a brand new version of Firefox that represents a complete rewrite of the browser. The release of an update for Safari by Apple in January 2018 should also significantly improve the browser’s security status.
Browserscope carries out ongoing tests on Safari, Chrome, Firefox, Opera, and Internet Explorer and they rank the Safari browser as the second safest option.
Apple currently seems to have a better security team working on its iOS system because whenever a security issue arises, such as Meltdown and Spectre, the patch for iOS seems to be released first. However, the company still has a very quick turnaround on updates for macOS and Safari.
The security of a browser can be measured by the resources that the company that produced it puts into continuous support and improvement. By this measure, Safari does very well.
The second strand of protection that you want from your browser after security is privacy. Apple has put a lot of work into this area and offers Safari users the option to block all tracker codes and remove cookies.
Unfortunately, this solution doesn’t quite eradicate the problem because the browser will only erase cookies 24 hours after they have downloaded, not block them completely. Worse still, if you revisit the domain that those cookies relate to, the cookies will not be removed even if they relate to tangential divisions or pages that you never return to. Web giants Facebook and Google can rely on the fact that each web surfer visits their sites with such frequency that they can keep their cookies alive.
Google Chrome
Chrome topped the rankings for security both in the Project Zero study and in Browserscope’s tests. If you are thinking of switch from using Safari, you should opt for Google Chrome.
Many people, however, are suspicious of Google because of its size and success. There are several levels of privacy and security that you need to be concerned about when considering a browser for your Mac. On the main issue of protection from viruses, cross-site scripting, encryption and authentication loopholes, and detection of malicious websites, Chrome should be your first choice.
Using the yardstick of Google’s security team quality and the number of updates that the company issues to protect users from attacks, this browser is second to none. In one update in July 2017, Google blocked 30 security vulnerabilities in Chrome.
Take advantage of the Chrome Incognito option to enhance your privacy. The Incognito option can be achieved by pressing Control-Shift-N while already in the browser. When you close down an Incognito window, all cookies and web form data is destroyed. Browser history is also removed for that session. Although the Incognito mode of Chrome doesn’t block browser fingerprinting, it prevents trackers from carrying over into other site visits as long as you remember to close and reopen the browser between site visits.
Those who still don’t trust Google will find information on privacy and security extensions later on in this guide.
Firefox
Google’s Chrome is the hands-down winner in the race to tempt Mac users away from Apple’s own Safari browser. However, if you worry about the corporate omnipotence of Google and you would rather not install Chrome, then Firefox should be your first port of call.
Firefox has a very impressive heritage. It is operated by the Mozilla Foundation and it inherited the code of the Netscape browser. Netscape invented HTTPS, so this is a very impressive parentage in terms of security. Mozilla is a not-for-profit organization and so it has no ulterior motive or advantage in hijacking your internet pleasure for its own gain.
The Electronic Frontier Foundation, which is an internet freedom pressure group, is particularly favorable towards Firefox and makes its free privacy utilities available for Firefox before it creates versions for other browser types.
Towards the end of 2017, Mozilla released a complete rewrite of its Firefox browser, which includes beefed-up security features and anti-tracking measures. The importance of this new version, which is officially recorded as Firefox 57, is so significant, that the organization gave this revamp a name: Firefox Quantum.
If you installed Firefox on your Mac some time ago, you need to get the update because Firefox Quantum is possibly one of the most secure browsers available today.
Opera
Opera is not one of the big contenders in the browser industry and some people find that appealing. The short version of analysis of Opera is that it isn’t as secure as Safari, so if you are looking for a reason to move away from the browser that comes ready-installed on your Mac, there aren’t many that point to Opera.
The Opera browser doesn’t fare well in regular tests. In fact, it comes way down on the list behind the much-maligned and discontinued Internet Explorer. Be particularly cautious about using the VPN built into the Opera browser.
Browser security extensions
You can enhance the privacy and security of your web surfing on a Mac by adding specialist extensions to your browser. In this section we look at five areas of your browser’s capabilities that can be strengthened. Unfortunately, the best protective extensions are not available for all browser types. However, we have picked the best free/cheap extensions to keep you safe with Chrome, Firefox, and Safari.
Tracker and ad blocking
Although the Safari browser has a native tracker blocker, as you read above, these functions don’t do away with tracking and adware completely. Google Chrome and Firefox also have tracking blockers, but these can always be enhanced.
The Electronic Frontier Foundation is an activist group that campaigns for net neutrality and internet freedom. The organization came up with its own browser extensions to help the general public block moves by big corporations to encroach on their enjoyment of the web.
The first of these EFF utilities is Privacy Badger. This utility will block tracker codes and the ads that rely on them. Advertisements that are embedded into web pages are not blocked by this utility. This utility can be installed on Chrome and Firefox.
Unfortunately, Privacy Badger is not available for Safari. So, use Adblock Plus instead. This is an enormously popular advert blocking system that you can use for free. The makers do ask for a donation. Although this utility won’t block tracker codes, it will block Google and Facebook ads, which are allowed through by Safaris’ native tracker blocker.
JavaScript blockers
The EFF also produces a free extension that blocks JavaScript from running in a web page. JavaScript is a programming language that can reach outside of your browser and install extra code on your Mac. The EFF JavaScript blocker is called NoScript. Sadly, this extension is only available for Mozilla Firefox.
If you use a Chrome browser, then you should consider ScriptSafe as a JavaScript blocker. This extension is free to use.
Neither ScriptSafe nor NoScript are available for Safari. However, JSBlocker has all of the JavaScript blocking capabilities that you need, plus a few other facilities. This extension will block trackers and adverts and it also prevents web servers from browser fingerprinting by blocking the querying of user agent information. This extension is free to use, but the developers give you the option of making a donation.
Web encryption enforcement
When you see “https://” at the front of a web page’s address, you can be sure that all of the content of that page is encrypted in transmission. This includes any information you type into web forms. This is great news for ecommerce sites. However, not every website uses HTTPS.
The HTTPS Everywhere utility creates HTTPS-like protection on transfers of web sites that don’t use the HTTPS schema. This is a really great tool that is provided by the EFF for free. Unfortunately, it is only available for Chrome and Firefox. There is no equivalent extension for Safari.
Password Manager
Password management is a very important element of web security. You should use different passwords for each site that you use and change those passwords regularly. Unfortunately, the easy-to-remember passwords such as “123456789” and “password” are worse than useless because anyone can guess them.
Instead, use a password manager. You need to remember the password for that utility, but after that, you won’t have to retain any other passwords in your head. LastPass generates passwords that are impossible to guess and changes them frequently. LastPass has a free version and it works with Chrome, Firefox, and Safari.
Browser Cleaner
Even if you are extra cautious and use the Chrome Incognito setting, you are still going to end up with some unwanted files attached to your browser. You can get temporary files, browser history, cache, cookies, and other stored browser information deleted with Click&Clean. This extension will wipe out Chrome records automatically, or on demand.
You can’t install Click&Clean on Firefox Quantum, so use eCleaner instead. The add-on puts a button on your browser. Pushing the button cleans out your browser files.
Neither Click&Clean nor eCleaner have versions for Safari. The Safari Cleaner extension is a respectable alternative.
Online threats
Security and privacy measures need to be extended beyond your Mac to the connections you make over the internet. The procedures and conventions of network communications that dominate data exchange on the internet all operate in plain text.
Internet vulnerabilities
Communications across the internet occur in chunks of data, called packets. The header of the packet contains addressing information. When you communicate with a web server using the HTTPS schema to get a secure web page, the contents of those packets are encrypted. However, the header information remains in plain text.
The admin information on internet connections can be valuable to many people. Header information has to be legible by routers, otherwise that information could not be forwarded on to its destination. Although you never see those addresses, governments and internet service providers are able to use them to impose controls on your web access. Even websites themselves can use internet addresses to block access to their content.
The standard for internet address is contained in the Internet Protocol, so these addresses are called IP addresses. The IP address on the internet has to be unique in the world. The pool of internet address is controlled by a central global authority and the allocation of each address is recorded to prevent the same address from being allocated twice.
Government website bans
The public process of IP address allocation means that each address can be traced to a specific user and a specific location. Each website has to be located at its host server. That host has an IP address. Therefore, anyone reading the packets leaving your computer can look at the destination address and work out which website you are contacting.
The ease with which the destination address can be read is what gives governments the ability to ban websites. You can’t get on the internet without signing up to an internet service provider. If you don’t have internet at home, but go out to a café that has free wifi, you are still being given access to the internet by a telecommunications company.
Everyone’s internet communications have to travel through an internet service provider. When a government wants to ban a website, they just have to order all ISPs in the country to drop any requests traveling to the IP address of that site. If you can’t contact a website’s host, you can never get a copy of any of the pages of that site.
Some governments, such as China and Iran, have a long list of banned sites. Although developed nations may seem liberal, just about all of them ban some websites. Access to BitTorrent index sites, for example, is blocked in a lot of advanced nations in the world.
Advanced government web access controls can go further. For example, it is possible to examine the contents of the packets returned by a web server. These packets contain the code that will be assembled by your browser into a web page. A practice called “Deep packet inspection” enables ISPs to read inside the packets to see the text that will appear in the web page. In this system, which is also known as “content filtering” the computers of the ISP scan for a list of words. If any of those alert words appear in the arriving code, the ISP simply doesn’t pass the code for that page on to you.
HTTPS encrypts the contents of packets carrying secure web pages. So that blocks government controls on content. However, the simple practice of blacklisting IP addresses still manages to create extreme restrictions on web access.
Some governments alter the records in the domain name system to make it impossible to reach a website. As you read in the description of OSX/MaMi, above, the domain name system translates between web addresses and internet addresses. China is known to practice.
Institutional block
Governments are not the only organizations that practice web access blocks. Educational institutions and workplaces also block access to websites that are considered “inappropriate” or offensive. So, if you fancy surfing the web from your Mac at work, you will find that there are a lot of sites that you cannot get through to. Even if you take in your own Macbook, you will not be able to access certain sites from your college or workplace.
There are methods to dodge government and corporate bans on website access. However, before we look at those solutions, there is one more type of web restriction to consider.
Regional restrictions
You don’t just to contend with ISPs and network owners blocking access to websites by reading the destination addresses of you connections. Some websites read the source address in requests for web pages and selectively block some requests. Regional restrictions prevent overseas access to some websites.
In this case, you are not prevented from reaching the website. However, the site owners have designed their presentation in such a way that it is impossible to access certain content. Some sites have several different versions for different parts in the world. For example, news websites will have a national edition and an international edition. If you access the news service’s site from outside the company’s country of operation, the site will redirect you to the international version. This is made possible by the location associated with your IP address.
Other sites will let you access the main pages of the website, but refuse to deliver you certain content. This strategy is particularly common among video streaming sites. The reason for these restrictions lies with the copyright obligations of the company that owns the website.
TV broadcasters are licensed to transmit entertainment in one country, or even just in one area of a country. Nowadays, TV stations put their shows on their website. Often you can watch channels live over the internet as they are broadcast over transmitters. They also have libraries of on-demand shows that have already been broadcast on their terrestrial channels.
The TV stations buy the right to show a production within their territory of operation. They can broadcast it through transmitters or satellites and over cable. At the same time they can transmit their content over the internet. However, they cannot allow people outside their operating region to access that internet content because then they would be in breach of their copyright agreements with the production companies.
In the next section you will learn how to free yourself from the restrictions that the plain text addresses in your internet connections allow companies and governments to impose.
VPNs for Macs
You can change your IP address as far as the world is concerned without the involvement of your ISP. An online service called a “Virtual private network,” or VPN, allocates you a new IP address in one of a range of offered locations. Not all VPNs have the same list of server locations. If you want to get into regionally restricted sites for a particular country, you need to make sure that you channel your traffic through a VPN server in that country.
The communication between your Mac and the VPN server is entirely encrypted. That means more than just the content encryption performed by HTTPS because the header information is encrypted as well.
You need to install a VPN client app on your Mac. That manages all of the internet communications from your computer while it is turned on. All of the packets in your connections need legible addresses on the front of them, otherwise the routers on the internet would not be able to pass them on. The VPN system gets around that problem by embedding the entirely encrypted packets inside carrying packets, which are addressed to the VPN server.
When the VPN is operational, all that your ISP gateway will see is that you have a lot of traffic back and forth to one particular address. As the address is that of the VPN server, all of your traffic gets through because it is not addressed to any of the banned addresses for which your ISP is searching.
VPNs also usually operate their own DNS server, or direct users to a trusted third-party system. That service gets around the trick that some authorities use in poisoning default DNS servers to remove the addresses of banned websites.
Governments and websites that want to control internet and web access are aware that VPNs exist, so they also check for VPN activity and try to block it. China is particularly keen to limit the access of its people to outside influences and has invested a lot of effort into trying to trap VPNs.
Because ISPs and regionally restricted websites look for VPN traffic, it is important that you only opt for the very best VPN services that can evade detection.
You can read more about VPNs for Mac is the Comparitech feature article on VPNs for Macs. The recommended VPN services in that article are:
ExpressVPN
ExpressVPN has one of the largest server networks in the industry, with a presence in 94 countries. This VPN is very good at getting around the regional restrictions on websites. This includes Netflix, which has some of the toughest location checks online. The app for Macs is really easy to use and you can also install the system on your router and on your iOS and Android mobile devices.
NordVPN
NordVPN allows you six simultaneous connections — ExpressVPN only gives you three. You can get into Netflix and evade detection in restrictive countries with NordVPN. This VPN can be installed on Macs and also be installed on mobile devices and routers. The NordVPN website includes instructions on how to install the system on 29 different router types. If you have the VPN running on your router, that counts as only one of the six connection allowance, even though it will cover all of the devices in your home, not just your Mac.
IPVanish
IPVanish has a custom-built infrastructure and they manage it all in-house. The company is based in the United States. However, they keep no records at all of customer activities so there is no paper trail should the NSA come knocking. You get an allowance of five simultaneous connections with IPVanish and the system can be installed on Macs. You can put this VPN on your router and it will also work on your mobile devices.
CyberGhost
The CyberGhost app has a really cool look and feel to it. Those design features should appeal to style-conscious Mac owners. The app works well on Macs and it opens with a configuration pre-screen. You press a button that describes your intended activity on the net and the system reconfigures itself to optimize for that. This app also works well on mobile devices and the VPN can be loaded onto routers. You get an allowance five simultaneous connections to the service.
PrivateVPN
PrivateVPN is a great option for those who like to download. The network is fast and the app is very easy to use. PrivateVPN doesn’t have servers in as many countries as the others on this list. However, all the major developed nations are represented. You get an allowance of six simultaneous connections with this service.
Email vulnerability
When you send an email to someone, you probably think that the email transmission system delivers that message straight to that person’s inbox. It doesn’t. The email transfer method is broken into two sections. The first part of the process delivers your email to an email server, to which your correspondent is registered. With that delivery, your email program’s job is done. The second part of the process requires the email client of the recipient to pull down the email from the server so the person receiving the email can read it.
Your email could be sitting on an email server for a long time. Not only does the process rely on all the notifications going through to the recipient’s mail client successfully, but the process that downloads emails doesn’t always delete them from the server. So even after it has been delivered and read, a copy of your email could be floating around on a computer somewhere on the internet.
Worse still, emails are not encrypted. They are not encrypted during transmission and they remain in plain text while they are at rest on the email server. This is a great source of information for hackers, blackmailers, and spies.
Although there are a number of email security systems available, not many of them are totally satisfactory and could leave your information at risk of exposure.
Email security for Macs
The Mail app on a Mac has encryption capabilities built-in. Since Sierra, that encryption is applied automatically. The system uses Secure/Multipurpose Internet Mail Extensions, or S/MIME for short. This seems to be good news. However, S/MIME isn’t nearly good enough to secure your email.
If you use webmail systems, such as Yahoo Mail, Gmail, or Outlook.com, the transmission of your emails to the mail server are protected by HTTPS encryption. However, although this seems to protect your emails and give you privacy, it doesn’t.
A fundamental problem with both HTTPS and S/MIME protection for emails is that both operate only during the transmission of an email. Once those emails arrive at the mail server, the encryption is stripped off and everything you wrote sits there in plain text. As explained above, it may be sitting there for years, even after the recipient has read the email.
Email servers aren’t so secure. There have been many revelations on emails being hacked in recent years. You may think that in order to steal your emails, someone would have to break into your house, work out the password for your Mac and get into your email app. Hackers don’t bother breaking windows because they know how to get into mail servers.
In order to protect your emails, you need to introduce extra security.
You can encrypt all of the text of your email yourself. However, then you will have the problem of getting the encryption key to all of the people that you want to send emails to and all of those people will also have to use the same encryption cipher. Stand-alone encryption systems can be expensive and end up being very difficult to manage.
In order to get full security for your emails, you will have to give up using Mail on the Mac, and abandon the big name webmail systems. There are some very good secure email systems available for Macs and many of them are free to use. Take a look at this list of some of the best encrypted email systems on the market today.
ProtonMail
This mail system uses S/MIME for email transfers and keeps emails in an encrypted state when they are on the mail server. There is an app for iOS, but no native app for Macs. However, you can access your Proton Mail inbox at the company’s website through your browser. You still get the same level of security. The encryption of emails is performed in the email client and even the Proton Mail company couldn’t get into your emails and read them. You can get a free account with Proton Mail that has volume restrictions: you can only send up to 150 emails and you only get 500 MB of storage.
Hushmail
Hushmail is also accessed through a browser on the Mac and there is an app for iOS devices. With this system, email transmission is protected by HTTPS and contents are encrypted so that they cannot be read by anyone when they are stored on the mail server.
If you send an email to someone who is also a Hushmail subscriber, the delivery of mail stays within the company’s system. In fact, even if you send an email to someone who isn’t a subscriber to the service, the text of your email never leaves the secure server of Hushmail. Instead, the recipient is sent a link where they can read the email through a secure browser. However, in the case of sending emails to non-members, you set up a challenge question that the recipient must answer in order to get access.
FlowCrypt
If you can’t live without Gmail, then try FlowCrypt. This is an extension for Chrome and Firefox browsers that adds a new button to the standard Gmail Compose form. This button gives you the option of adding encryption to an email before you start writing it. The FlowCrypt method deploys Pretty Good Privacy, which is a widely used methodology to create “end-to-end encryption.” This means than no one, other than the sender and recipient of an email can get hold of the encryption key — not even Google.
If you send an email to another FlowCrypt user, the system takes care of the encryption key distribution. If you send a secure email to a non-member, you have to set up a password, which the recipient must enter in order to read the mail. In this case, you will need to use some other method to deliver that password, such as a secure chat app, or a telephone call. You can get a 14-day free trial to test the service and there is a 60-day money-back guarantee when you sign up for a year.
Common sense tips for Mac users
The most important security measure you can employ to keep you Mac safe is common sense. Sometimes, you just really, really want a piece of software or a movie and you don’t want to pay for it. In these circumstances, you take risks — you look all over the web for it and consider downloading from sites or through systems that shouldn’t really be trusted. If you take time to consider your needs, those immediate risk strategies fade.
Similarly, employ caution with emails that make offers that seem too good to be true. If you adjust your expectations and decide that you won’t be rushed or bedazzled by exciting marketing, then your life in general will be more secure, not just your Mac.
Beyond basic attitude, there are other steps that you can take to secure your Mac and preserve your privacy:
Backups
As you read in this guide, some rootkits and ransomware viruses just cannot be recovered from. In these instances, you are likely to lose everything stored on your Mac in order to clean the system. Therefore, backup your files regularly. If you use USB storage or an external drive, be careful to disconnect it after the backup. Do not keep your external storage attached at all times. This is because the Mac regards these attached devices as just another drive and a rootkit or ransomware can use operating system routines to ruin those just as quickly as internal storage.
Cloud storage can be a good idea. However, keeping that connection open all the time will slow down all of your other internet connections and infected files will be uploaded, overwriting your original versions. Make sure that the cloud storage has rollback, so if damaged files do get backed up, you can sort through to earlier snapshots and recover the original versions.
Contact methods
Surprisingly, chat apps are much more secure than regular email systems. The Signal app is particularly secure and WhatsApp uses that system’s security measures. Facebook owns WhatsApp and has also adopted the Signal protocol for its Messenger system. However, in Facebook Messenger, you need to know about the security option and turn it on.
Don’t give too much information about your life in social media sites. One of the main hacker methods for targeting you is to look up your Facebook page or read your Twitter feeds. Be aware that cybercriminals are like stalkers and they will exploit any information you give away to break into your email and steal your identity.
Software updates
It is very important to keep up with the latest versions of all of the apps that you have running on your Mac. If you have the option of turning off automatic updates for the apps on your computer, don’t take it. You should particularly allow the operating system to update itself whenever necessary. Many of those updates and security patches to close off the latest exploit that hackers have discovered.
Vary passwords
Do not use the same password for every website and internet service that you access. When phishing campaigns get you to disclose your email password, those hackers will get automatic access to everywhere else that you visit on the web. The importance of securing your email account is crucial. So many sites have a “I forgot my password” option that allows you to reset your password through an email link. Many of these do not include challenge questions. Those that do can be circumvented by hackers that have researched your posts on social media and know the likely answers to those questions.
Use a password locker system to vary the passwords used at the internet services to which you subscribe.
Two-factor authentication
Look for online services that use two-factor authentication, which is often written as 2FA. This security method requires a second identity verification method other than the password. This second factor is usually linked to a physical piece of equipment, such as a code generator. Online banking frequently uses 2FA to protect against online hacking.
The code generator means that the hacker would actually have to break into your home and steal the gadget in order to get into your account. As hackers work remotely and operate in mass volume, it isn’t cost effective to visit the homes of all their victims. Common housebreakers may get hold of your code generator, but they would be unlikely to have the skills to break your password, or find out which online service the code generator relates to.
Conclusion
Macs have delivered top-class security to their owners since the early days of personal computers. However, there is a battle going on over the internet right now and the intensity of that fight is only going to deepen.
Forget all of those web articles that tell you that Macs are immune from viruses. The extensive list of viruses, worms, Trojans, and online threats detailed in this guide is just a summary of the top threats that you face on your Mac. The real situation is a lot more threatening, and it is only going to get worse.
Hacking is a very lucrative business and it is expanding across the globe. As computer and internet access gets cheaper with each year, the number of desperate people that can make easy money by attacking your Mac increases.
Your plan of action should be:
- Install antimalware software
- Get a VPN
- Protect your email with encryption or switch to messaging
- Use a password manager and change your passwords frequently
- Avoid downloading from unknown sources
- Choose not to access email attachments
- Employ caution and skepticism when presented with incredible offers
- Allow automatic updates of trusted apps
- Upgrade to the latest version of macOS
- Control the personal information that you give away on social media
There are many people in this world who have had bad experiences with security breaches that have cost them dearly. Have you been hacked? Have you lost your Macbook and discovered that the person who found it managed to get into your bank account? Often, you only realize the security measures you need to take after it is too late. If you have security and privacy advice for fellow Mac users, then share your intelligence in the comments section below.
Image credits:
- Computer virus illustration by Santeri Viinamäki, licensed under CC BY-SA 4.0
- A blue malware being by Clker-Free-Vector-Images, licensed under CC0
- A neon colored computer by Anti Virus 777, licensed under CC BY-SA 3.0
- Trojan horse in Canakkale,Turkey by Stryngford, licensed under Copyrighted free use
- Visuele voorstelling van een botnet by JeroenT96, licensed under CC BY-SA 4.0
- Diagram depicting the life cycle … APT by Dell SecureWorks, licensed under CC BY-SA 3.0
- White Keyboard … by Macedo_Media, licensed under CC0
- Web browsers via Flickr by Sean MacEntee, licensed under CC BY 2.0













































Thanks for this incredible writeup. The best article on Mac security and privacy I have ever read. One thing I might add. For prevention of ransomware threats, I have found and use the app called “Ransomwhere?”. I am not affiliated with them, but recommend it because I believe it gives excellent mitigation against unknown programs encrypting your data. That is, as long as you know your system and what apps legitimately encrypt data.